The Audit Connection Blog
Stay cyber safe during Cybersecurity Awareness Month
October ushers in the official fall—leaves scattering on the sidewalks, longer nights and a chilling breeze. The month of October also has special significance here at the State Auditor’s Office—Cybersecurity Awareness Month. All month long, we will be sharing cybersecurity resources to help governments of all sizes stay cyber safe. ... CONTINUE READING
Every government in Washington has a duty to safeguard the resources entrusted to it; our new guide shows you how
Segregation of duties, or separating conflicting duty assignments in your government, can help protect your local government’s assets. But which duties do you segregate, and what are your options if you cannot feasibly do this? What if you are a very small entity with limited resources? Our Office recognizes how challenging this can be, so the Center for Government Innovation created a new resource to help you get started, no matter your size. ... CONTINUE READING
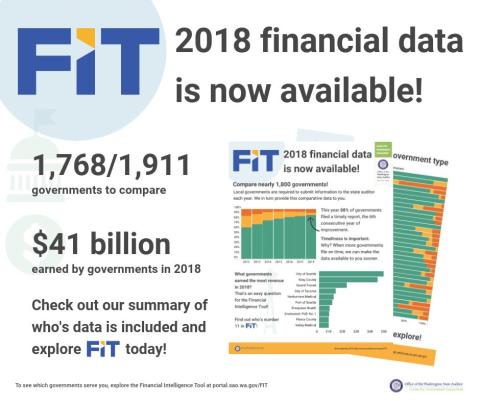
2018 Financial Data is Now Available!
The Financial Intelligence Tool (FIT) now contains the most recent financial information from nearly 1,800 local governments! ... CONTINUE READING
SAO passes peer review with flying colors
The Office of the Washington State Auditor recently passed its external peer review, which is a rigorous independent examination of the Office’s work conducted every three years. ... CONTINUE READING
SAO Roadshow taking the place of BARS Roundtables this fall
The Office of the Washington State Auditor is pleased to announce a new, expanded fall outreach event that takes the place of the BARS Roundtables. The SAO Roadshow will travel to a location near you beginning in October and offer a full day of assistance and training. ... CONTINUE READING
IT and facilities departments both can #BeCyberSmart
The Center for Government Innovation has developed two new cybersecurity resources to help local government professionals in IT departments but also in facilities departments as well. These resources provide guidance that is easy to understand and use. ... CONTINUE READING
Where are your payments going this month?
It is common practice to use automated clearing house (ACH) systems to pay state and local government employees and vendors. However, frauds associated with ACH systems are rising dramatically, particularly for direct deposit paychecks. ... CONTINUE READING
SAO now issues public report on each fraud investigation
To meet stakeholders' needs and increase transparency, going forward SAO will report all fraud investigations through a public report that will be published on our website. In the past, smaller losses had been reported to management in a letter rather than in a public report. ... CONTINUE READING
New manager takes helm of South King County office
Saundra Groshong, audit manager for our South King County team, has left SAO after 19 years of service. Taking her place as team audit manager is Alex Beherndt. ... CONTINUE READING
More ways to #BeCyberSmart for the finance and legal departments of local governments
Cybersecurity is complex, and it can be hard to understand what your role is in keeping your organization safe from threats. The Center for Government Innovation has developed two new resources specifically for finance and legal staff at local governments. Staff in these departments play an important role in cybersecurity, and these resources provide understandable and actionable guidance and relevant information. ... CONTINUE READING